
Android malware continues to evolve and gain scary new capabilities, like the Chameleon Banking Trojan that was first detected in early 2023. A new update of the malicious app gives it incredible new powers, like blocking fingerprint authentication so it can your phone’s PIN code or password.
Most Android users should not worry about Chameleon as long as they only download apps from the Google Play store and know how to avoid phishing scams online. Chameleon can only be installed on your device if you download apps from third-party sites.
The latest Chameleon malware can come in the form of a Chrome browser app. The dangerous malware is attached to the app, so you think you’re getting a genuine Google product. The fix is simple here: Search for apps on the Play Store and don’t install apps from anywhere else.
The cybersecurity researchers at ThreatFabric detailed the newly evolved version of Chameleon.
One of the upgrades the malware got is extended reach. It’s been found in the UK and Italy, while the original versions targeted Android users only in Australia and Poland. The early version of the trojan already had dangerous capabilities, targeting a user’s banking and crypto apps:
This banking trojan displayed a distinctive capability to manipulate a victim’s device, executing actions on the victim’s behalf through a proxy feature. This feature enables advanced maneuvers like Account Takeover (ATO) and Device Takeover (DTO) attacks, particularly targeting banking applications and cryptocurrency services. These functionalities relied on the abuse of Accessibility Service privileges.
In Australia, it disguised itself as apps from official institutions, such as the Australian Taxation Office (ATO). In Poland, it masqueraded as popular mobile banking apps.
The updated version seen spreading in Europe poses as Google Chrome downloads.
Once installed, Chameleon will try to do two things: Enable Accessibility Services and turn off biometric prompts.
For the former, the malware will look for the Android version of the phone. If it detects Android 13 or later, it’ll display an HTML page guiding the user through a process that enables Accessibility Services on the device. The page will provide step-by-step guidance and might look like a genuine help page to unsuspecting victims.
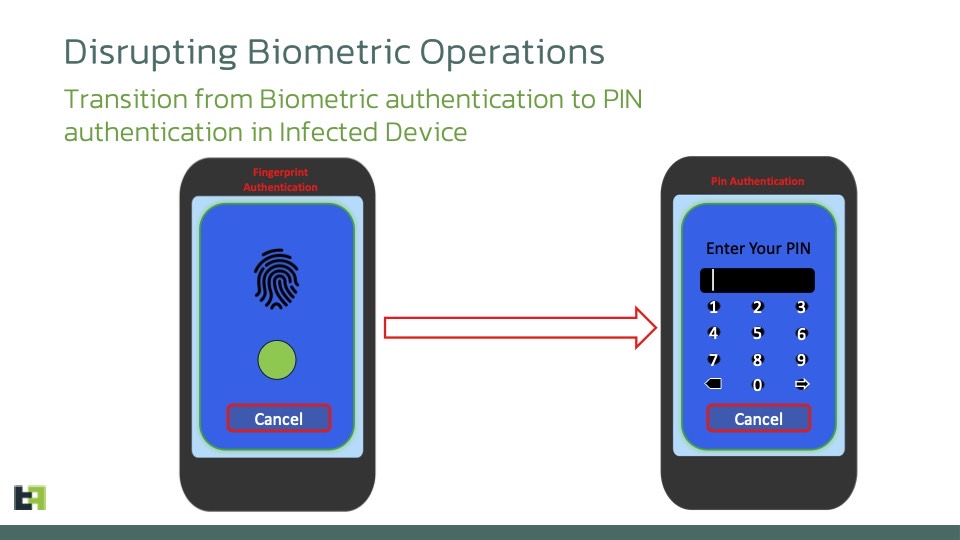
The second new power that Chameleon got is the ability to disable biometric authentication in favor of the PIN:
This method employs the KeyguardManager API and AccessibilityEvent to assess the screen and keyguard status. It evaluates the keyguard’s state concerning various locking mechanisms, such as pattern, PIN, or password. Upon meeting the specified conditions, the malware utilizes the AccessibilityEvent action to transition from biometric authentication to PIN authentication. This bypasses the biometric prompt, allowing the trojan to unlock the device at will.
This feature will let the malware steal PINs and passwords via a keylogger. This could allow thieves to actually steal and use the handset.
Alternatively, forcing a PIN authentication might be convenient if hackers can use the malware to operate the handset remotely. They could unlock the screen and apps protected by the same fingerprint and password combination. While that’s speculation, it’s clear that Chameleon is a more advanced, more dangerous version than the early 2023 variant.
Finally, the researchers at ThreatFarbic say Chameleon also has improved task scheduling features and can adapt to the apps the user might use on the device. The malware might inject features into an app, like displaying fake screens that might look genuine if accessibility features are turned on. Otherwise, the malware might collect data about the apps that are in the foreground.
Google is aware of the threat and told The Hacker News that Play Protect will guard users from the threat:
The emergence of the new Chameleon banking trojan is another example of the sophisticated and adaptive threat landscape within the Android ecosystem. Evolving from its earlier iteration, this variant demonstrates increased resilience and advanced new features.
But ultimately, it’s up to you to avoid downloading apps from untrusted sources. That means never clicking on suspicious links you might receive via email or instant chat apps. All that goes double if you have a phone without Google Play Services installed. That’s the only way to get that Play Protect feature that Google has enabled by default on devices with the Google Play store installed.
I’ll also say that if you own an Android phone that lacks support for Google apps, you probably should avoid trying to download these Google apps from anywhere. That’s how you might get into trouble.

